1 Information security
1.1 History
The evolution of information security since the 1980s, BS and ISO standards
Other information security proverbs and quotes
The information, hardware and software that an organizationa structure that satisfies a need (see also ISO 9000, 3.3.1) owns is a valuable investment that must be protected. One of the best ways to take care of this treasure is to set up an Information Security Management System (ISMS).
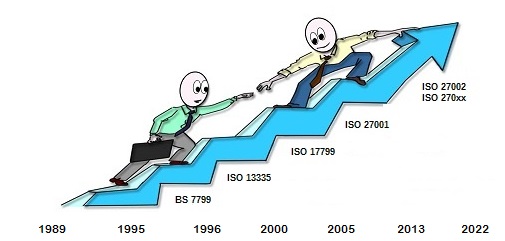
In 1989, the User’s Code of Practice was released, based on Shell's security policy, at the request of the UK government (Department of Trade and Industry).
In 1995, the British standard BS 7799 was published.
In 1996, the ISO 13335 standard was published, which after its last version in 2004 will be replaced by ISO / IEC 27001.
ISOinternational organization for standardization (International Organization for Standardization) was created in 1947. ISOinternational organization for standardization comes from the Greek for "isos" (equal). For simplicity, we use ISOinternational organization for standardization instead of ISO / IEC.
The history of transformations and versions of the ISO 27000 family of standards is shown in figure 1-1.
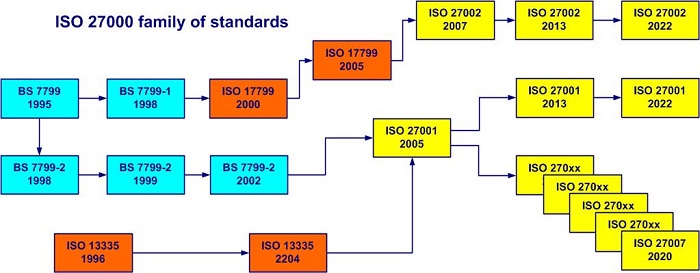
Figure 1-1. History of the ISO 27000 family of standards
Since 2005, ISO / IEC 27001: 2005 has offered the possibility of certification of an information security management system. More details you can see at ISO SC 27 Journal, Volume 2, Issue 2 dated July 2022, dedicated to ISO/IEC 27002:2022.
At the beginning of 2022, the new version of ISO 27002 was released and at the end of 2022, the new version of ISO 27001 "Information security, cybersecurity and privacy protection — Information security management system — Requirements” was released. For more details see paragraph 2.1.
1.2 Scope
Scope of information security
Information security is everyone's business
The ISO 27001 standard is generic because it applies to the management system of any organizationa structure that satisfies a need (see also ISO 9000, 3.3.1), without any constraints relating to the size, activity or type. It is an international voluntary standard that allows certification by an accredited (certification) body.
The implementation of an information security management system always:
- results from a strategic decision by top management
- agrees with:
- the objectives of the organization
- corporate culture
- business processes
Applying the ISO 27001 standard and complying with its requirementsexplicit or implicit need or expectation (see also ISO 9000, 3.1.2) helps preserve the confidentiality, integrity, availability and traceability of information in the organizationa structure that satisfies a need (see also ISO 9000, 3.3.1)..
Compliance with the requirementsexplicit or implicit need or expectation (see also ISO 9000, 3.1.2) related to the assessment and treatment of risks (based on the ISO 31000 standard) helps to reassure interested parties about the management of information security.
1.3 Principles and steps
Properties of information security, quality management principles, preparation and implementation of an ISMS, Deming cycle
Security is a process. John Mallery
The information security (IS) approach is a state of mind that starts with top management as a priority strategic decision and extends to all staff. Top management defines the information security policy, in which the information security objectives are set, which are applicable to all activities. The tool used to achieve the objectives is the information security management system, of which prevention is the essential concept.
The three essential properties of information security are confidentiality, integrity and availability as shown in Figure 1-2.
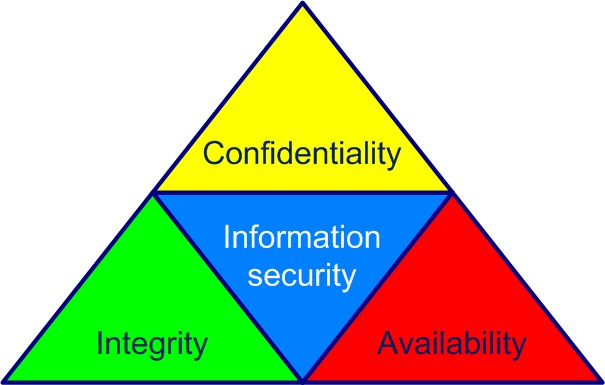
Figure 1-2. Information security properties
Take your bank account as an example. Account information must be protected for:
- its confidentiality - the information must remain secret
- its integrity - the total information must be accurate and must not change
- its availability - the information must remain accessible in a timely manner
Any information security management system includes three distinct and interdependent approaches:
- process approach
- risk-based thinking
- continual improvement
The seven principles of quality management (cf. figure 1-3) will help us obtain sustainable performance (cf. ISO 9000: 2015, § 2.3).
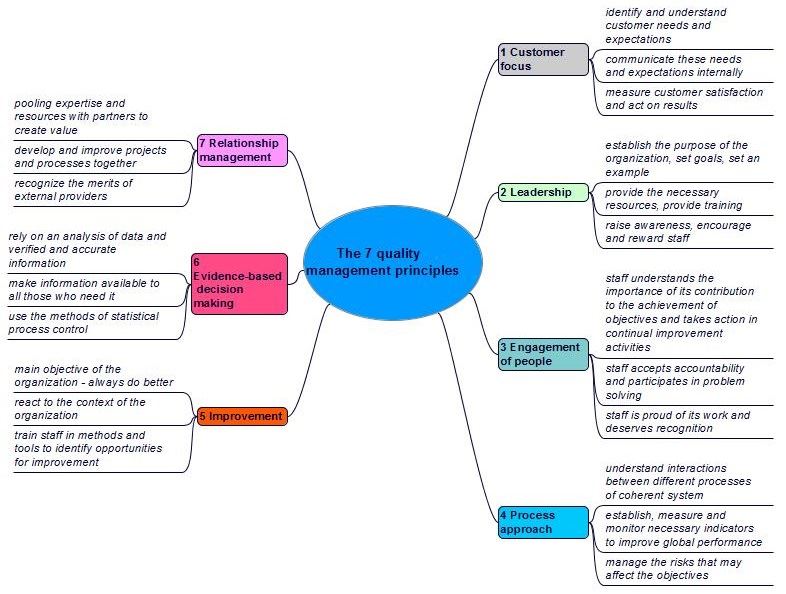
Figure 1-3. The 7 quality management principles
A well-prepared approach is half successful
The processactivities which transform inputs into outputs (see also ISO 9000, 3.4.1) for implementing an information security management system involves several steps. An example of preparation is shown in Figure 1-4.
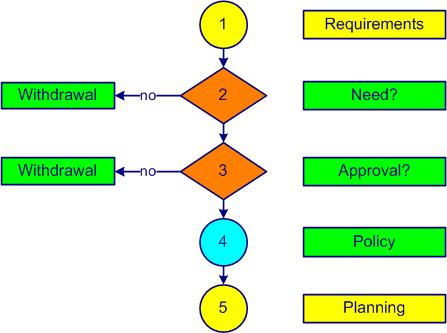
Figure 1-4. ISMS preparation
Step 1 involves identifying the needs and expectations (requirements) of interested parties:
- staff
- customers, consumers
- competitors
- shareholders, investors
- external providers (suppliers, subcontractors, partners)
- organizations and branch associations
- statutory and regulatory authorities
The involvement of top management at its highest level is truly indispensable. The advice of a consultant is often solicited. Determining the current status of the management system (whole or partial) would be welcome at this stage. An external certification body is chosen.
One of the key questions that arises quickly (step 2) is the need for this decision. If this is not really necessary or if the estimated costs of the certification approach exceed the available resources, it is better to reject this idea immediately.
The benefits of implementing an information security management system are often:
- increased security of information systems
- enhanced resistance to threats and malware
- the information is only available to people who have permission
- the information is protected against any modification by unauthorized personnel
- improved protection of:
- operational information
- business secrets
- intellectual property
- personal data
- better defined responsibilities and obligations
- decreased likelihood of occurrence of information security incidents
- high level of risk control
- business disruptions avoided
- reduced insurance costs
- active involvement of staff in improving information security
- updated legal obligations
- strong integration of information security into business processes
- culture of continual improvement of information security
- you can sleep more peacefully

The benefits of the certification of an information security management system are often:
- an improved image of the company
- being one step ahead of the competition
- new customers
- improved confidence of interested parties
- increased market share
- an increase in sales
- better financial performance
More than one and a half million businesses worldwide cannot be wrong!
IBM, one of the world's leaders in information technology, has implemented ISO 27001 to improve the security of its IT systems and protect its sensitive data. The standardization of procedures and the establishment of an IT security culture have made it possible to reduce the risks of cyberattacks and data theft.
IBM recorded significant improvement in IT security, demonstrating the company's commitment to protecting customer and employee data and the importance of prevention in IT security.
The third step shall determine whether this approach receives the approval of the staff. A communication campaign is launched in-house on the objectives of an information security management system (ISMS). The staff is aware and understands that, without their participation, the project cannot succeed.
Have confidence: success will come with the involvement and effort of all!
The vision (what we want to be), the mission (why we exist) and the business plan of the company are determined. The following step (4) includes the establishment of an outline of the information security policy and objectives. If you do not have a copy of the ISO 27001 standard, now is the time to get it (cf. sub-clause 2.1 of the present course).
Planning is the last step (5) of the project preparation for obtaining ISO 27001 certification. A reasonable period is between 12 to 24 months (each company is unique and specific). The financial resources and staff are confirmed by top management. A management representative is appointed as project leader. Top management commitment is formalized in a document communicated to all staff. A person is appointed as project leader for obtaining ISO 27001 certification.
The establishment and implementation of an ISO 27001 information security management system are shown in figure 1-5.
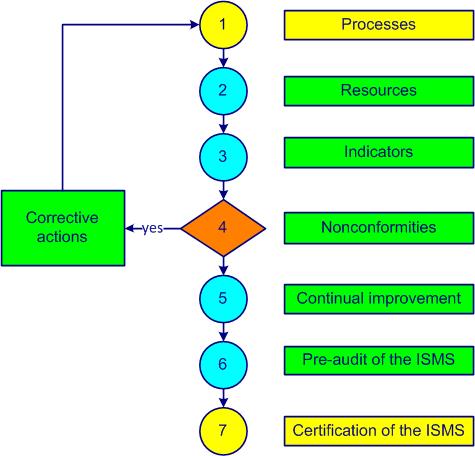
Figure 1-5. ISMS implementation
Step 1 aims to identify and determine the processes, interactions, owners, responsibilities and drafts of certain documented information. The first versions of processactivities which transform inputs into outputs (see also ISO 9000, 3.4.1) sheets, job descriptions and work instructions are written with the participation of the maximum number of available persons.
The necessary resources to achieve the information security objectives are determined in step 2. Planning tasks, responsibilities and time frames are established. Training of internal auditors is taken into account.
Step 3 allows you to set and implement methods for measuring the effectiveness and efficiency of each processactivities which transform inputs into outputs (see also ISO 9000, 3.4.1). Internal audits help to evaluate the degree of implementation of the systemset of interacting processes (see also ISO 9000, 3.2.1).
Nonconformities of all kinds are listed in step 4. A first draft for dealing with waste is established. Corrective actions are implemented and documented.
A first encounter with the tools and application areas of continual improvement occurs in step 5. Risks are determined, actions are planned and opportunities for improvement are seized. An approach to preventing nonconformities and eliminating causes is established. Internal and external communication is established and formalized.
To conduct the tepre-audit of the ISMS (step 6), documented information is checked and approved by the appropriate people. A management review allows the evaluation of compliance with applicable requirementsexplicit or implicit need or expectation (see also ISO 9000, 3.1.2). The information security policy and objectives are finalized. An information security manager from another company or a consultant can provide valuable feedback, suggestions and recommendations.
When the systemset of interacting processes (see also ISO 9000, 3.2.1) is accurately implemented and followed, the certification of the ISMS by an external body is a breeze and just a formality (step 7).
An example of a certification project plan with 26 steps is shown in annex 01. 
An appropriate method for evaluating the performance of your information security management system is the RADAR logic model of excellence EFQM (European Foundation for Quality Management) with its nine criteria and overall score of 1000 points.
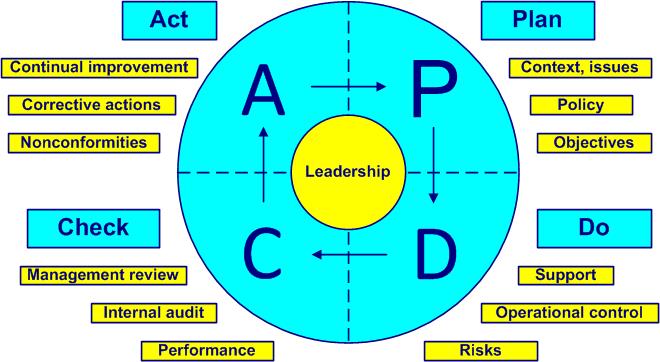
The Deming cycle (figure 1-5) is applied to control any processactivities which transform inputs into outputs (see also ISO 9000, 3.4.1). The PDCA cycles (Plan, Do, Check, Act) are a universal base for continual improvementpermanent process allowing the improvement of the global performance of the organization (see also ISO 9000, 3.2.13 and ISO 14 001, 3.2).
- Plan – define context, issues and processes, demonstrate leadership, establish policy and objectives (clauses 4, 5 and 6)
- Do – realize the product, treat risks, develop, implement and control processes, demonstrate leadership and bring support (clauses 5, 7 and 8)
- Check – compare, verify, evaluate risks, performance, inspect, analyze data, conduct audits and management reviews and demonstrate leadership (clauses 5 and 9)
- Act – adapt, demonstrate leadership, treat nonconformities, react with corrective actions and find new improvements (new PDCA cycle), (clauses 5 and 10)
For more information on the Deming cycle and its 14 points of management theory, you can consult the classic book "Out of the crisis", W. Edwards Deming, MIT press, 1982.